
前言
菜是原罪
Misc
Secret
下载下来是个压缩包,解一下伪加密,得到一个名为Secret的文件,16进制查看以后发现存在IHDR这个Png文件的标志位,故推测这是个png文件,但缺少了头部的89 50 4E 47这四个字节,补齐,改拓展名为png即可,可以看到一堆HEX,转ASCII即为flag。
A_Beautiful_Picture
改一下IHDR就能看到flag
Easybaba
binwalk一下,发现有zip,提取出来,里面有个里面全是出题人.jpg,实际上这是个avi文件,然后avi抽帧,有好多二维码,每个二维码能扫出来一部分flag,组合起来是一串base16,解码得到疑似flag的字符串,看着像栅栏,但实际上不是,但是都是单词。。。还有很明显的恶搞意味,修改修改顺序就得到flag。
BJD{imagin_love_Y1ng}
小姐姐-y1ng
16进制查看器打开以后搜BJD即可。。。
Real_EasyBaBa
这题已吐…看着WP都难搞……

圣火昭昭
这道题目相比于其他脑洞杂项题,还是有一些可以学习的新知识点的。

TARGZ-y1ng
套娃题目,全当练算法了,WP说压缩了300层。。。。也就是300层套娃。。。压缩包的名字就是解压密码。。。
有个坑点…这些都是zip,但拓展名都是tar.gz
1 | # -*- coding: UTF-8 -*- |
1 | [*] error or finished! |
运行就能拿到一个名为flag的文件,里面就是flag。
脚本都跑了二十二秒多…. 手动解压的话估计要累到死。。。
运行结果显示总共套了298层娃。。。。
Imagin开场曲
挺有意思的杂项,就纯听力题…
不过通过这个题了解到一个挺好玩的东西叫Mikutap
BJD{MIKUTAP3313313}
Reverse
guessgame
IDA加载,Shift+F12即可看到flag。。。。。。
8086
这题考察汇编。
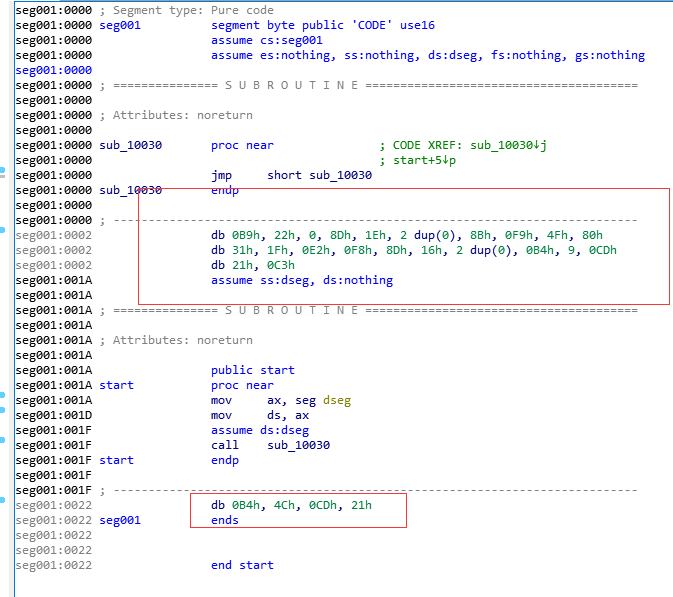
但一些代码被IDA识别为数据了,按C还原为代码,即可看到程序的逻辑
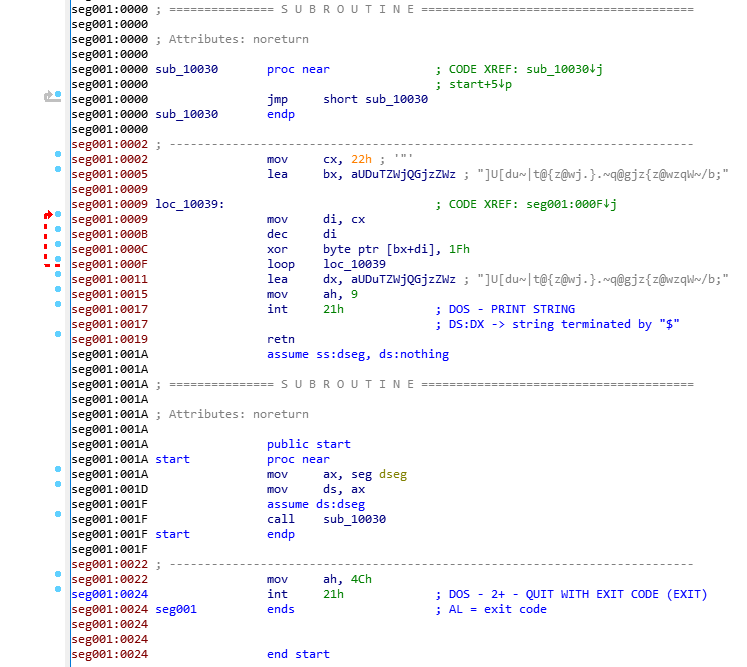
所以对这个字符串]U[du~|t@{z@wj.}.~q@gjz{z@wzqW~/b;进行与0x1f异或的操作即可
flag: BJD{jack_de_hu1b1an_xuede_henHa0}
Pwn
写在前面
本次CTF的pwn题大部分都是Ubuntu19.04的,libc是libc-2.29.so,但通过patchelf依然可以在其他版本的U buntu上进行本地调试。
r2t3
1 | Arch: i386-32-little |
存在后门函数0x804858B dl_registery()调用system('/bin/sh')
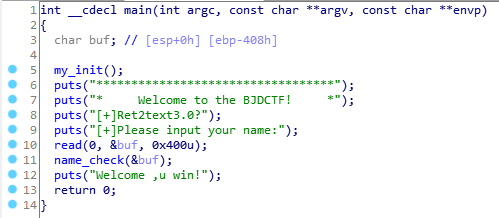
main函数的read处没有栈溢出,接着看name_check
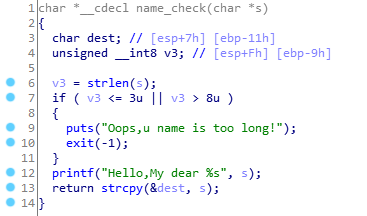
这里的strcpy可以操作一波,但是需要先绕过前面的长度检测,来看一下汇编
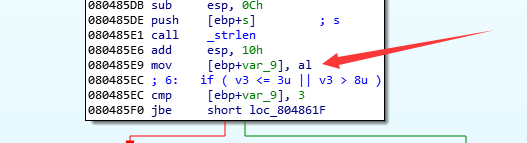
可以看到这里,调用完strlen以后长度保存在eax中,而这里是令v3 = al然后再进行的长度验证,也就是说真正验证的是长度的低字节。
所以就可以先构造好payload,然后payload = payload.ljust(size,'a'),size取0x1040x108或者0x2040x208或者… 只要让它低字节在0x04~0x08之间即可,当然也不能超过read的size。还有一点需要注意,sendline相比send要多出一个\n,这也占size的。
1 | from pwn import * |
one_gadget
1 | Arch: amd64-64-little |
程序保护全开
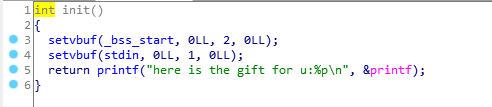
但是在init函数里面存在一个leak,泄露了printf的地址,而且题目也提供了libc,所以可以泄露出libcbase
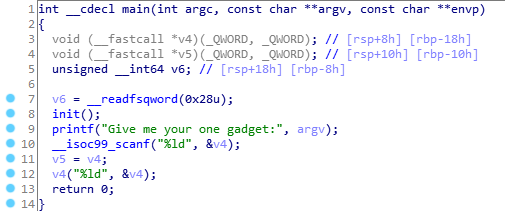
main函数也格外的和谐,直接读入one_gadget然后调用…
1 | one_gadget libc-2.29.so |
这里似乎只有第四个能用
1 | from pwn import * |
ydsneedgirlfriend2
真·入门级堆题,感谢出题人不杀之恩。
1 | Arch: amd64-64-little |
题目提供4个功能
1 | 1.add a girlfriend |
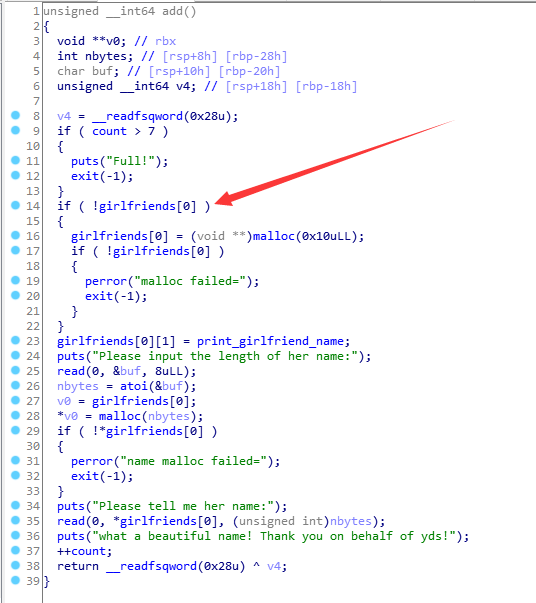
其中add里面,只会在第一次add的时候在girlfriends[0]申请0x10大小的堆块。
在*girlfriends[0]存放的是最新一次add时,申请的name的chunk。
在*girlfriends[1]存放的是print_girlfriend_name的函数指针。
delete函数存在UAF漏洞,free掉但未置为NULL。
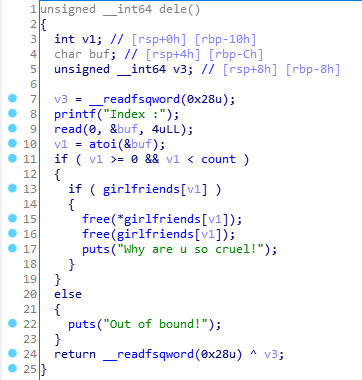
而且出题人太贴心了,给了backdoor函数
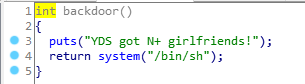
思路较为简单,借助Fastbin的FILO特性,结合delete函数中的free顺序可得
1 | add(0x10,'aaaa') |
完整EXP
1 | from pwn import * |
r2t4
1 | Arch: amd64-64-little |
main函数有明显的格式化字符串漏洞和栈溢出,但只溢出了8个字节,只够覆盖掉rbp

存在backdoor函数,调用system('cat flag')
看了半天没想起来怎么做,canary过不掉。。。赛后看了wp以后…

既然canary过不掉,那就直接故意触发吧,修改__stack_chk_fail_got为backdoor即可。。。。
这里我之前写的fmtstr_payload64生成的payload的长度为0x40,超出read的size了,很无奈,只能按short类型来手动写了。
1 | from pwn import * |
secret
1 | Arch: amd64-64-little |
挺蛋疼的一道题目
让你猜秘密,实际上就是猜数字,虽然这些数字在IDA中都能通过正则表达式匹配出来。。。但是一共1万个!!
有的老哥真匹配出来然后send了一万次….被BUU封IP了….
官方WP里的做法就比较巧妙
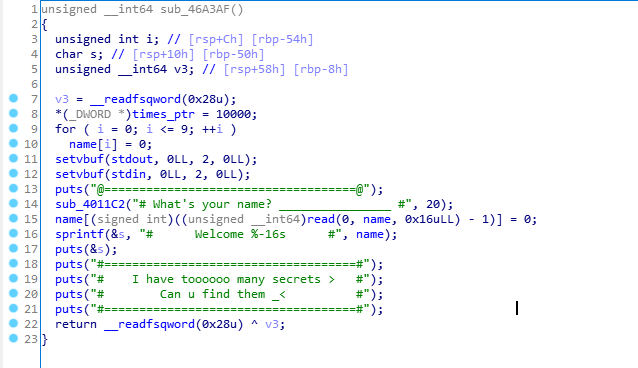 name实际大小为0x10,但却read了0x16个字节
name实际大小为0x10,但却read了0x16个字节
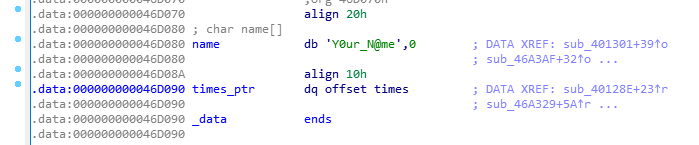
而name与times_ptr紧邻,多出的6个字节可以用来覆盖times_ptr
注意这里是times_ptr,这是个指针,指向真实的times
程序初始times = 10000,每猜对一次,times -= 1。
程序给出了system函数,而且当猜错以后会调用printf(name);
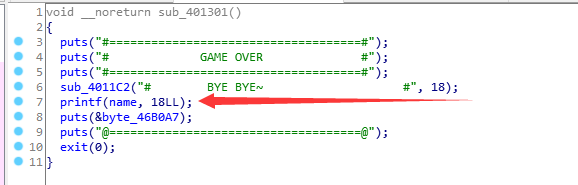
起初想着能不能利用这个格式化字符串漏洞,但是仔细想了想,似乎不太可行。
但是我们可以通过修改printf_got为system,令name以/bin/sh;开头,触发system(‘/bin/sh’)
1 | pwndbg> got |
可以看到printf@plt + 6 = 0x401086 , system@plt + 6 = 0x401076只相差0x10。
加之每猜对一次,times -= 1,我们可以通过溢出覆盖times_ptr为0x46d040,然后答对一定的次数,让printf_got变为system_plt,然后故意答错,触发printf(name)即触发system('/bin/sh')
这里有一点需要注意:官方WP给的是答对0x10次,让printf_got变成0x401076也就是system@plt + 6,但是亲测打不通,调试以后发现其他一切正常,但是调用system的时候报段错误…这里我试了一下,答对0x14或者0x15次,也就是让printf_got变成system@plt+2或者system@plt+1才可。

附上EXP:
1 | from pwn import * |
Crypto
签到-y1ng
base64,decode一下就好了。
老文盲了
脑洞够大。
罼雧締眔擴灝淛匶襫黼瀬鎶軄鶛驕鳓哵眔鞹鰝
这句话的谐音就是BJD大括号这就是福莱格(flag)直接交了吧大括号
所以flag为BJD{淛匶襫黼瀬鎶軄鶛驕鳓哵}
燕言燕语-y1ng
1 | 小燕子,穿花衣,年年春天来这里,我问燕子你为啥来,燕子说: |
给了一串HEX,转ASCII以后是yanzi ZJQ{xilzv_iqssuhoc_suzjg}
猜测是维吉尼亚密码,密钥是yanzi,成功解密
flag为BJD{yanzi_jiushige_shabi}
cat_flag
小猫很可爱。

从上往下,每一行代表一个二进制数,吃饭团的表示0,吃鸡腿的表示1
bin转ascii得到flag。
BJD{M!a0~}
灵能精通-y1ng
这题有点水,赛后看WP才知道这个密码是圣堂武士密码,通过查题目的题干能知道这是星际争霸里面的一个角色的一个技能台词??!!

Y1nglish-y1ng
给了一个txt
1 | Nkbaslk ds sef aslckdqdqst. Sef aslckdqdqst qo lzqtbw usf ufkoplkt zth oscpslsfko. Dpkfk zfk uqjk dwcko su dscqao qt dpqo aslckdqdqst, kzap su npqap qo jkfw mzoqa. Qu wse zfk qtdkfkodkh qt tkdnsfw okaefqdw, nkbaslk ds czfdqaqczdk. Bkd lk dkbb wse z odsfw. |
下面有类似于flag的东西,但开头不是BJD而是MIH,盲猜维吉尼亚密码。
quipqiup在线解密,指定MIH=BJD,可以得到
1 | Welcome to our competition. Our competition is mainly for freshmen and sophomores. There are five types of topics in this competition, each of which is very basic. If you are interested in networy security, welcome to participate. Let me tell you a story. I was having dinner at a restaurant when Harry Steele came in, he is a Japanese from Japan but now he is not living in Japan, maybe Harry isn't a Japanese name but he is really a Japanese. Harry woryed in a lawyer's office years ago, but he is now worying at a bany. He gets a good salary, but he always borrows money from his friends and never pays it bacy. Harry saw me and came andsatat the same table. He has never borrowed money from me. While he was eating, I asyed him to lend me &2. To my surprise, he gave me the money immediately. 'I have never borrrowed any money from you,' Harry said,'so now you can pay for my dinner!' Now i will give you what you want. BJD{pyth0n_Brut3_f0rc3_oR_quipquip_AI_Cr4cy} |
但是提交一直不成功,修改Cr4cy为Cr4zy也不成功,去群里看了看公告,发现有地方需要改。

读了读上面那段话,发现那段话里面该是k的地方全变成了y,所以修改Cr4cy为Cr4ck。
BJD{pyth0n_Brut3_f0rc3_oR_quipquip_AI_Cr4ck}
rsa0
nc连接以后有如下回显,好像因为靶机不同,具体的回显也不同
1 | e=15549851 |
….直接解出来p和q 然后…直接做就行…
1 | import gmpy2 |
rsa1
同样是靶机不同,回显不同
和rsa0一样,不过这个要根据完全平方公式推出来p和q、尝试过得出来pq(也就是n)以后直接分解n,但是分解难度太大,所以还是根据完全平方公式推p和q吧。
有一处是需要对(p+q)^2进行开放,普通的math.sqrt()方法因为这个数太大了而会报错,这里需要用gmpy2.iroot(gg,2),gg代表(p+q)^2,很幸运,正好开平方,也就是得到的结果进行平方以后正好等于(p+q)^2
得到pqec以后脚本和rsa0就一样了。

